Banks and other financial institutions are, by their nature, high security environments. They demand the most robust systems to protect both physical assets and highly sensitive data. These buildings must be equipped with watertight security. Knowing who is inside the building and where they are at any given time is an essential part of this strategy.
Designers, specifiers, and installers of high security access control systems know that no two projects are identical. Every bank and financial institution’s premises is in a unique situation, with unique requirements for security and access. These buildings must combine rigorous security with the need for efficiency, as well as offer a publicly accessible area.
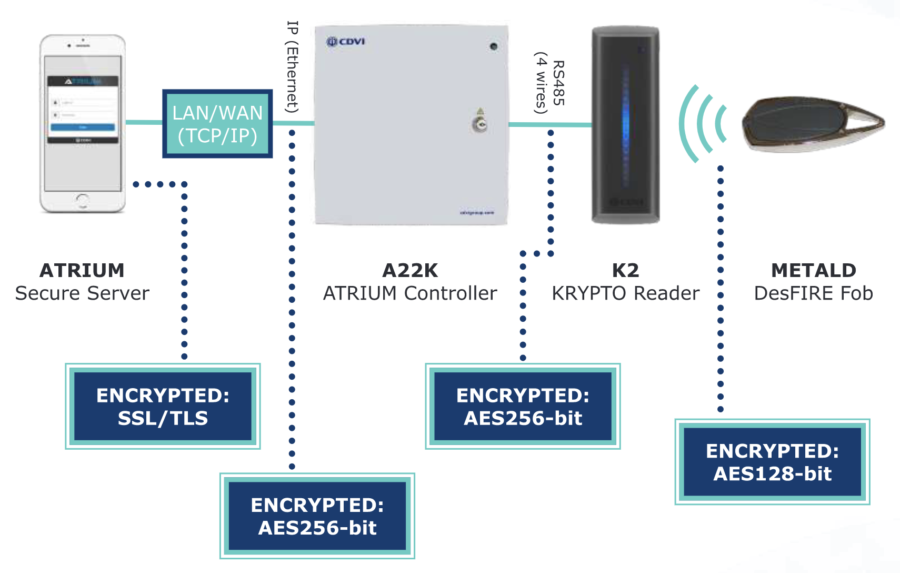
End-to-end encryption
KRYPTO is an ultra-high security version of our trusted ATRIUM access control system. Equipped with military-grade AES encryption, KRYPTO automatically creates unique authentication keys for each site and each credential, so that data is robustly protected throughout the system. Card cloning, a significant risk factor for high security environments, is made impossible by the AES block cypher.
There’s no manual configuration required to set up encryption in the KRYPTO system. Straight out of the box, it’s all done for you.



Reliable capacity management
The A22K controller, equipped with AES encryption, also offers a built-in counting function that makes it easy to set up sophisticated security protocols. As people enter or exit a given area, they present their credentials and the controller instantly updates its capacity log for that area. When the pre-defined occupancy limit for that area is reached, all the doors to the area are automatically locked and won’t allow anyone else to enter until a space is freed.
